SASE Explained: Definition, Benefits, and Best Practice
Secure Access Service Edge (SASE) combines WAN edge services with Secure Service Edge tools and services to securely connect remote users and sites to data, cloud services, and the enterprise.

What is SASE?
Secure Access Service Edge (SASE) is an enterprise networking technology category introduced by Gartner in 2019. It converges the functions of network and security solutions into a unified, global cloud-native service.
SASE allows an architectural transformation of enterprise networking and security. That, in turn, lets IT provide an agile and adaptable service to its users. It is typically delivered as a service, but enterprises can also combine WAN and security services into their own managed SASE solution.
One of the challenges those new to SASE technology often encounter is that solutions can be quite complex as they are made up of many discrete elements. One way to better understand what SASE is and what it does is to look at those elements.
The elements within most offerings and assembled solutions fit into two categories. There are WAN Edge Services and Security Service Edge (SSE) elements.
Elements of a SASE Cloud Infrastructure
WAN Edge Services | Security Service Edge |
|---|---|
SD-WAN WAN optimization Quality of Service (QoS) Routing Content delivery Caching SaaS acceleration | Secure Web Gateway Cloud-access Security Broker (CASB) Encryption/decryption Firewall or Firewall-as-a-Service Virtual Private Network (VPN) Zero-Trust Network Access (ZTNA) |
A complete SASE implementation melds many (all) of these elements into a single solution. An enterprise can select the elements it wants, work with the different vendors and providers, and bring them all together into a complete solution. Or, given the complexity of such an integration, and the fact that many enterprises may not have expertise in every category of product or service, more common approaches are to:
Work with a web security vendor who can help the enterprise integrate the WAN services.
Work with a network services provider who can help add security services.
Get a complete offering as a managed service from a vendor or cloud services provider.
The role of standards

SASE-standards-2-DWK4CA.jpg
SASE security is new to many enterprises, so most have a dearth of expertise in the various elements that comprise a complete solution. Additionally, there are many different solutions that must be tightly integrated for a successful SASE implementation. The solutions come from a wide range of vendors and providers. And most offerings have never had to interoperate and work together before.
All these factors make standards all the more important. Fortunately, there is help in this area thanks to MEF, the global industry association of network, cloud, and technology providers.
On the subject of the importance of standards, Pascal Menezes, CTO of MEF, noted:
Enterprises need to ensure that networking and security teams integrate their systems together into a cohesive, synergistic solution that works efficiently to best meet the needs of the organization. Additionally, a fragmented vendor ecosystem and lack of common terminology leave enterprises challenged to compare SASE feature sets and solutions. The resulting confusion can lead to incomplete service offerings that don't meet needs and expectations.
To simplify and speed up the evaluation, implementation, and management of SASE services, MEF published the industry's first standard for SASE, which defines common terminology, attributes of the service, and a service framework, along with a Zero Trust framework.
MEF's SASE standard and Zero Trust framework help simplify offerings and provide clarity when selecting SASE components. Enterprises can make choices based on industry-standard definitions allowing for easier evaluation and faster decision-making and implementation.
What made SASE necessary?

SASE-2-2-GDNWY5.jpg
Until the pandemic, SASE's adoption was limited. A 2021 industry survey of 750 IT leaders, including CIOs, CTOs, IT, and network directors, found that less than 12% of enterprises fully embraced the framework before the pandemic. Part of the problem was confusion about what SASE technology is. One-third of the 750 professionals surveyed could not even confidently define SASE components.
That said, interest in and adoption of the technology exploded thanks to the networking and security challenges of the pandemic. Traditionally, enterprises used firewalls and enterprise VPNs to secure network traffic through an encrypted tunnel. These measures were already becoming obsolete in a world where data was increasingly distributed and perimeter-less.
With the advent of work-from-anywhere business models, these issues that made traditional remote access hard to carry off are simply compounded. Network traffic patterns radically changed, forcing new thinking about connectivity and security.
In other words, now that enterprises simply don't use the old hub-and-spoke topology that routed remote users' network traffic through a single data center, neither should their modern security frameworks. Transitioning from traditional network security models, network administrators shifted to cloud-centric security strategies that let people securely work from anywhere.
Bottom line: SASE networking is designed for today's perimeter-less environments. It eliminates the need to force traffic through a central site and makes it easier for remote groups to work over distributed networks securely.
Additionally, SASE security is the right fit for modern enterprises. Why? The nature of what needs to be connected and protected has changed. More users are accessing cloud services, and edge devices are proliferating.
One of the challenges of implementing SASE networks and SASE security is the complexity of marrying the multiple elements of a solution into one offering. As we noted in What to Consider when Selecting a SASE Provider:
Picking the right SASE solution does not need to be a complicated decision for organizations. Setting goals, establishing network and security requirements, understanding the right questions to ask, and knowing the important capabilities will help organizations come away with a SASE architecture that provides long-term network performance and cyber security protection without excessive costs or complications in the future.
What are the benefits of using SASE?

SASE-3-2-J50GBK.jpg
The path to security modernization requires new thinking. For years, security was added on as an overlay to networking solutions. But because networks and threats have changed, so too must security evolve as well.
In today's network-connected devices and the work-from-anywhere world, users and devices move between on-premises locations, interconnected branch locations, home offices, and temporary locations during travel.
So, enterprises need solutions that integrate networking and security. Many are adopting SASE components that meld networking services, typically based on SD-WAN, with security technologies, including Zero Trust Network Access (ZTNA) and Secure Service Edge (SSE). These security approaches shift the focal point of security to the user or device.
The various elements that are merged together into SASE provide a solution that delivers many benefits, including:
1. Better security and data protection
The larger and more diverse your infrastructure, the more your SASE networking approach will need to deliver all the security you require now without limiting your options for the future. As we noted in Getting SASE? Four Guidelines for Success:
SASE provides secure connectivity for all the remote devices accessing your network and applications. As such, security and risk management leaders should build a migration plan from legacy perimeter and hardware-based offerings to a SASE model.
To that end, SASE technology makes use of many security functions that help reduce cyber threats and safeguard data and systems. Some of the capabilities and protections provided in a common SASE implementation include the following:
Secure web gateway, which protects users from web-based threats while applying and enforcing corporate acceptable use policies.
Cloud-access Security Broker (CASB), which is an on-premises or cloud-based security policy enforcement point between cloud service users and providers.
Encryption, which encodes data so that it remains hidden from or inaccessible to unauthorized users.
Firewall, which keeps out unauthorized traffic and only lets in communications that are deemed safe, using a set of security rules.
Virtual Private Network (VPN), which brings privacy to communications over a public or untrusted data network.
Zero-Trust Network Access (ZTNA), which provides secure remote access to an enterprise's applications, data, and services based on clearly defined access control policies.
2. Increased efficiency and productivity
Users can work from anywhere with SASE security. They can access cloud and enterprise apps and services in the same way, no matter where they are. That reduces the amount of training needed and reduces remote access complexity.
From an IT perspective, every user or site is connected in the same way. The common approach is to bring a WAN link to the user or site. That link could be a home user's cable broadband connection or an enterprise's high-speed Internet service line. And then use either simple on-site or on-premises WAN gear to connect to a centrally managed SASE security service. That offloads many chores from the IT and security teams, thus improving their efficiency and productivity.
3. Increased agility and flexibility
SASE networking provides the agility and zero-trust capabilities that organizations need to adapt to today's changing threat landscape and connectivity needs of their users. By combining cloud-delivered networks and security, enterprises can easily adapt to fast changes. That was proven out during the pandemic when most enterprises went from at most 25 percent of their users working out of the office to almost 100 percent overnight.
Technologies like VPNs, Desktop-as-a-Service, and Virtual Desktop Infrastructures provided some relief. But SASE's additional benefits (beyond merely providing secure access) drew many enterprises to the technology and architecture. Now, SASE technology is routinely used to quickly support new initiatives at a pace that matches the speed of business.
This capability has the potential to do so much more than security. As we noted in How SASE Architectures Can Reach Beyond Cybersecurity:
SASE offers a dynamic service edge architecture that has the potential to become the next-generation foundation for enterprise networks of the future.
4. Improved user experience
SASE networking makes it easier for users to gain secure access to the data, applications, corporate resources, and cloud services they have privileges for. Connectivity is simplified, eliminating common problems other remote connectivity solutions might have that impact the user experience.
Additionally, many SASE offerings include advanced features, like load-balancing and QoS support, that can ensure a user has the bandwidth to conduct business. SASE vendors and providers are also adopting tools and techniques like AIOps and observability to ensure their networking and security infrastructure works at optimal levels. That helps to deliver a pleasant user experience.
We raised these points in SASE Should Make Life Easier for Employees and IT, where we noted:
As SASE solutions evolve to incorporate more user-centric intelligence, you can expect the enterprise IT stack to become even more dynamic and even more supportive of the real-world problems confronting enterprises every day.
5. Increased security of cloud-based resources
Several components of a SASE solution provide enhanced security of cloud resources. Zero Trust Network Access capabilities can be fine-tuned to only allow those with rights to specific cloud resources access to those resources. And another element of a SASE solution, a cloud access security broker (CASB), ensures security policy enforcement between users and the cloud services they are trying to access.
6. Improved network control
Many SASE solutions offer centralized, role-based management that helps network and IT managers run the performance of the solution to match the needs of their users and applications. Additionally, most SASE technology gives enterprise staff full visibility and control over their areas of responsibility, allowing them to apply appropriate policies to better manage network traffic.
7. Improved risk detection and prevention
Many SASE systems incorporate the latest risk detection and prevention technologies and solutions. For example, most integrate a next-gen firewall (or firewall-as-a-service) that helps identify and block known and suspect traffic from reaching the enterprise. Many SASE companies also incorporate the latest anti-phishing, anti-virus, and anti-malware in their solutions.
8. Cost savings
Cost savings when using a SASE solution typically come in lower operational spending. Many networking and security tasks commonly done by enterprise staff are offloaded to a vendor or provider. Other cost savings come in the form of not necessarily needing to train or hire staff with expertise in every functional aspect of a SASE security implementation.
9. Increased security compliance
SASE technology helps enterprises apply consistent security policy enforcement. When married to best practices, consistent policy enforcement helps enterprises meet the compliance regulations they are audited for every year. Additionally, SASE components enhance data protection, which can help enterprises meet today's increasingly more stringent data privacy regulations.
10. Improved security posture of the edge
The edge is all the rage today. Autos, web cameras, refrigerators, IoT devices on manufacturing product lines, smart health monitoring sensors, and more are connecting to enterprise networks and sharing data.
Every edge device is an entry point for a cyberattack. Thus, edge security is critical. SASE networking offers a way to securely connect edge devices and protect the data they send.
How do you use SASE?

SASE-4-2-HW2GPC.jpg
Enterprises have multiple ways to implement and use SASE components. They can use existing WAN services, like SD-WAN, and add on security solutions to build their own SASE solution.
Rather than the enterprise cobbling together a solution by adding security capabilities to an SD-WAN infrastructure, other options are to get an integrated offering from a single vendor or provider. The vendor offerings can be in the form of a one-time engagement where after all elements are acquired, the enterprise manages everything. Or the enterprise might opt for a managed service from the vendor.
As with any other decision about networks and infrastructure, the plus side of opting for a single source or managed service offering is that all elements of the SASE service are offloaded to the provider or vendor. The downside is that an enterprise might limit its ability to embrace new technologies and services as they emerge. Here are some things to consider to help select the right SASE solution for your enterprise.
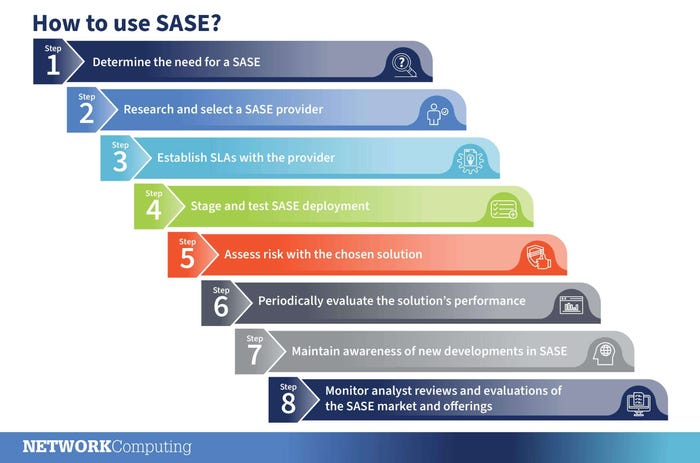
SASE Infographic-step diagram.jpg
Step 1: Determine the need for a SASE
The very first question to answer is, does my organization need SASE security? There are a plethora of secure networking offerings on the market today. What makes SASE technology necessary?
As we noted in The New Normal Requires a New Enterprise Security Framework:
Secure access requirements for enterprises have taken on a new paradigm. Some applications are on-premises, while others are in the cloud, and some users are on-site, while others are remote. Network security requires a new model that considers all scenarios and positions organizations for the move to SASE.
Additionally, there are a couple of common use cases that move an enterprise to adopt SASE security. They include:
A need for improved access: Today's workforce requires reliable access to applications from any location, using any device. SASE networking offers a consistent and secure experience and interface regardless of whether access is remote or on-premises. And a SASE solution also offers a comprehensive approach to security to protect devices, users, and data.
A need for improved security: The enterprise edge is no longer an easy-to-defend, single physical location. With users working from anywhere (home, office, on the road) and the need to support the growing number of IoT and smart devices, there is no logical place to put a traditional demarcation point between inside the enterprise and outside. A SASE approach modernizes cybersecurity across the organization's entire network architecture and simplifies and streamlines the management process, making it easier for teams with limited resources to support their modern workforce.
Step 2: Research and select a SASE provider
Enterprises need help evaluating their options when selecting SASE services. That's where standards and provider certifications can help.
A good place to start is MEF's SASE standard (MEF 117), which defines SASE service attributes and a SASE service framework. The standard specifies service attributes to be agreed upon between a service provider and a subscriber for SASE services, including security functions, policies, and connectivity services. The standard defines the behaviors of the SASE service that are externally visible to the subscriber irrespective of the implementation of the service. A SASE service based upon the framework defined in the standard ensures the provider's service provides secure access and secure connectivity of users, devices, or applications.
Another way to evaluate a SASE provider is to look at its certifications. MEF 3.0 certifications ensure a service provider's solution conforms to industry standards and offers peace of mind for enterprises that the services they purchase will perform as expected.
Step 3: Establish SLAs with the provider
SASE providers typically offer guarantees on service availability. These guarantees are put into contracts as uptime service level agreements (SLAs). Uptime is typically defined as the amount of time that a service is operational and available.
Uptime SLAs are typically expressed in terms of the availability percentage in a set period (daily, weekly, monthly, quarterly, or yearly). The SLAs are presented as how many 9s of availability. For example, a service offering four 9s of availability means the provider guarantees availability 99.99% of the time. Four 9s availability translates into an average 9-second downtime per day, 1-minute downtime per week, a 4-minute and 21-second downtime per month, and so on.
Estimated Downtime
Uptime SLA | Daily | Monthly | Weekly | Quarterly | Yearly |
|---|---|---|---|---|---|
99.9% (Three 9s) | 1m 26s | 43m 28s | 10m 4s | 2h 10m 24s | 8h 41m 38s |
99.99% (Four 9s) | 9s | 4m 21s | 1m | 13m 2s | 52m |
99.999% (Five 9s) | Less than 1s | 26s | 6s | 1m 18s | 5m 13s |
Some argue that enterprises should look for even more robust and resilient services. That would be five 9s uptime or an expectation that services would be available 99.999% of the time. That translates into less than a second, on average, of downtime a day, 6 seconds a week, or 26 seconds per month.
WAN service provider contracts also often include performance SLAs. That might include bandwidth SLAs (maximum upload and download speeds) and SLAs on latency and jitter.
Step 4: Stage and test SASE deployment
Do a Proof-of-Concept project with real locations and real users to see how well an offering meets your needs. Then test this implementation.
SASE service providers are obligated to deliver comprehensive service-level agreements (SLA) to their enterprise users. However, unlike traditional network and infrastructure SLAs, SASE KPIs have not been standardized and vary widely for each specific service and application. At the same time, SASE testing standards are just beginning to emerge. As a result, it is essential that an enterprise that is just starting to use SASE components establish a methodology to validate that service's end-to-end performance and behavior.
In addition to the network aspects of a SASE service, enterprises must test the security capabilities as well. Specifically, an enterprise should validate the efficacy of the security controls and their effectiveness and performance with respect to finding the optimum balance between quality of experience (QoE) and security effectiveness.
Step 5: Assess risk with the chosen solution
Not all SASE networking solutions are alike. Access controls and security can vary widely between solutions. Check to be sure the SASE solution's security capabilities provide more than an encrypted tunnel. This is critical because of the risks of today's advanced threats.
The solution must include multi-enterprise-grade security solutions that inspect traffic and detect and respond to known and unknown threats. For example, check to be sure there is an up-to-date secure web gateway that guards against the latest web-based attack attacks.
The SASE solution should have ZTNA, URL filtering, DNS security, anti-phishing, anti-virus, and anti-malware services that employ the strongest, most up-to-date approaches for safeguarding data, applications, and services.
Step 6: Periodically evaluate the solution's performance
The global, interconnected world is an incredibly dynamic place. An enterprise may have a finely tuned and highly optimized SASE solution when implemented. But will that be the case over time?
Many factors can degrade the performance of a cloud-based solution. A provider may fail to scale its infrastructure as it grows its business. That could lead to poorer performing services as more users and sessions consume more and more processing power. Similarly, there could be contention for network bandwidth as operations grow.
Even if a provider adequately scales to meet growing demand, small usage differences could impact a user, office, or region of a county. For example, a branch office with normal SASE performance levels might suddenly find a significant drop in performance if a new company moved to the same office park and used the same provider for its SASE services.
For all these reasons, enterprises should periodically test the performance of their SASE components to be sure they are getting the performance they signed up for and that their SLAs are being met.
Step 7: Maintain awareness of new developments in SASE
SASE technology combines many discrete network services and security point solutions (often delivered as a service). As a result, there are constant updates that an enterprise must be aware of to ensure they have the best solution for their needs. Vendors and providers of specific elements of a SASE solution might update their offerings. There might be new versions of a Cloud-access Security Broker (CASB), Zero-Trust Network Access (ZTNA), firewall, or secure web gateways (SWG) used in a complete solution. A new firewall might offer protection against newer cyberattacks, or a gateway provider might bundle in enhanced features like load balancing or selectable QoS.
Similarly, providers might up their ante. For instance, in 2022, some providers started offering malware catch-rate SLAs with their SASE services. Does yours? And some solution providers have added AIOps and automation to their offerings to troubleshoot and avoid problems more quickly, as well as lighten the load on the IT staff.
Step 8: Monitor analyst reviews and evaluations of the SASE market and offerings
Networking and security requirements are constantly changing. New SASE products, services, and technologies are always being introduced. And the vendor landscape keeps shifting.
That makes it imperative that enterprises keep pace with what is happening in the market. Many turn to industry analysts like Network Computing contributing editor Zeus Kerravala, founder and principal analyst with ZK Research. His Network Computing columns frequently cover new developments in network security and the SASE market.
Another common source for help is the series of Gartner Magic Quadrant reports. There are reports for many of the discrete aspects (e.g., firewalls) of a SASE solution. Gartner also puts out reports on Security Service Edge (SSE), a critical element of any SASE security implementation.
Checking these and other sources will help keep an enterprise appraised of changes in the SASE market.
FAQs

SASE-zero-trust-2F74MN7.jpg

SASE-zero-trust-2F74MN7.jpg
How does SASE architecture improve security?
A SASE architecture improves security by applying consistent policy enforcement. SASE delivers a comprehensive range of threat management services to any network edge and protects user systems and assets on-premises and off. Additionally, SASE technology provides a secure, consistent client-to-cloud user experience.
What are the components of a SASE network architecture?
A SASE network is typically comprised of different components. Most SASE network architectures make use of a common core set of elements. They typically WAN network services and a bevy of security services, including a Cloud-access Security Broker (CASB), Zero-Trust Network Access (ZTNA), Software-Defined Wide-Area Networking (SD-WAN), Firewall as a Service (FWaaS), Secure Web Gateways (SWG), and Centralized and Unified Management.
What are the advantages of using SASE for cloud data centers?
The initial benefit of the SASE networking model, and where most companies first deploy it, was to support remote employees. But increasingly, enterprises are interested in getting the same usability and management features and applying them to their existing wide-area networks and on-prem data centers. Specifically, enterprises are looking for simplification as they connect more devices to their infrastructure. SASE technology helps with that simplification.
How does SASE make use of Zero Trust Network Access (ZTNA)?
SASE and ZTNA are both important components of a modern security architecture. SASE provides a comprehensive, multi-faceted security framework, while Zero Trust Network Access (ZTNA) requires users and devices to provide explicit permission to access resources. When used together, they can provide a more comprehensive security solution that protects applications and data, regardless of the end user's location.
What is the impact of SASE on data protection capabilities?
SASE's approach to cybersecurity plays a crucial role in protecting today's distributed IT systems. SASE encrypts all communications and enables Intrusion Detection and Prevention Systems (IDPS), URL filtering, firewalls, and more. All these features help mitigate the threat of malware and hacking.
How is SASE used to improve IT infrastructure management?
SASE security is often delivered to an enterprise via a single service provider or as a managed service. That alone simplifies infrastructure and security management. Additionally, SASE helps solve network performance and limited security visibility commonly found in modern distributed networks. How? The single provider or managed service approach means the provider has more control over network performance, security visibility, and the overall user experience.
What is the difference between SASE and a cloud architecture model?
A cloud architecture combines virtualized back-end compute platforms and services (e.g., servers and storage) and an access/delivery network upon which applications can run. In contrast, SASE technology combines the network element of a cloud architecture, typically in the form of SD-WAN services, with security services.
How does SASE help protect against data breaches?
A typical SASE implementation includes multiple safeguards to prevent data breaches. Elements like a secure web gateway, cloud-access security broker, and firewall reduce the chance of attacks getting to a user or into the enterprise. Malicious sites, suspect emails, and more can be blocked.
Additionally, Zero Trust Network Access forces all users, internal and external, to verify who they are and whether they have the appropriate privileges to any data or application before they gain access. And finally, all data moving between users, sites, and the cloud is encrypted.
How does SASE reduce complexity when working with multiple security vendors?
SASE networking itself does not help. It is the way SASE components are consumed that makes the difference. Many enterprises work with a single provider or vendor. That entity would be responsible for managing the different security elements of a complete solution.
For example, many providers who deliver SD-WAN services have expanded their offerings by incorporating security services into a bundled SASE networking service. In this case, the provider offloads the tasks of managing multiple security vendors from the enterprise.
Similarly, a vendor offering SASE solutions would bundle the different security products and services into an offering that the vendor manages for its enterprise client.
SASE: The sum of many parts
Many enterprises are exploring or adopting SASE technology composed of a WAN services component and network security element. Understandably, bringing together multiple point solutions to enable complex service deployments can be challenging and lead to problems.
As a result, SASE security typically takes the form of a merged SD-WAN and SSE environment managed by a vendor or provider. The chief benefit of using SASE in this way is for enterprises to provide their increasingly distributed workforce with access to corporate resources in a manner that protects users, data, and the company.
About the Author
You May Also Like




