MPLS Traffic Engineering: Tunnel Setup
Traffic engineering can greatly improve performance in MPLS networks. Find out how specific traffic paths are defined and calculated using routing attributes and protocols.
May 8, 2014

Multi-Protocol Label Switching (MPLS) was created to improve packet performance in the core of the networks and is widely used for that purpose. It has also been adapted for other use cases, and one of the most important is traffic engineering.
If you already have MPLS deployed in your network -- perhaps for a VPN -- MPLS traffic engineering can be very beneficial. Here we'll discuss the additional steps that must be taken, the design criteria, and other design-centric questions that must be answered to do so.
In MPLS traffic engineering, all configurations are done on a specific network node called the headend or ingress node. Here is where all tunnels and constraints are created. Tunnel destination address is also specified at the headend. For example, if an MPLS traffic engineering tunnel will be set up between R2 and R6 in Figure 1, all the definitions are done at R2. The tunnel destinations are called tailend or egress node.
MPLS traffic engineering tunnels are unidirectional tunnels and not congruent. This means that if one tunnel is created to carry traffic between R2 and R6, the return tunnel from R6 to R2 is not created automatically. Reverse tunnels must also be created, but this time R6 is used as the headend and R2 as the tailend. The tailend has no configuration.
Figure 1: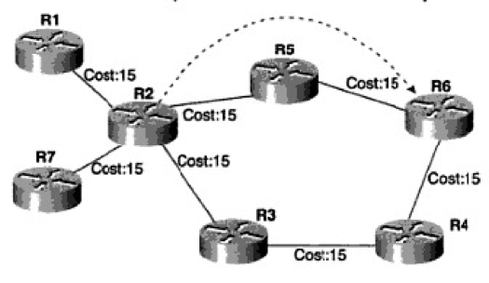 Figure 1
Figure 1
Four steps are required for MPLS traffic engineering to take place:
Link-state protocols carry link attributes in their link-state advertisements (LSAs) or link-state packets (LSPs).
Based on the constraints defined, the traffic path is calculated with the help of Constrained Shortest Path First (CSPF).
The path is signaled by Resource Reservation Protocol (RSVP).
Traffic is then sent to the MPLS traffic engineering tunnel.
Let's take a look these steps in detail:
1. By default, link-state protocols send only connected interface addresses and metric information to their neighbors. Based on this information, the Shortest Path First (SPF) algorithm creates a tree and builds the topology of the network. MPLS traffic engineering allows us to add some constraints. In Figure 1 above, let's assume the R2-R5 link is 5 Mbit/s; R5-R6 is 10 Mbit/s; and all the interfaces between the bottom routers are 6 Mbit/s.
If we want to set up a 6-Mbit/s tunnel, SPF will not even take the R2-R5-R6 path into consideration, because the link from R2 to R5 does not satisfy the minimum requirement.
In addition, we could assign an administrative attribute, also called a "color," to the link. For example, the R2-R5-R6 interfaces could be designated blue, and the R2-R3-R4-R6 route could be assigned red. At the headend, the constraint can then specify whether to use a path that contains a red or blue color.
The color/affinity information, as well as how much bandwidth must be available, reserved, and unreserved for the tunnel are carried within the link-state packet. In order to carry this information, some extensions have been added to the link-state protocols. Open Shortest Path First (OSPF) carries this information in the Opaque LSA (or Type 10 LSA), and Intermediate System to Intermediate System (IS-IS) uses TLV 22 and 135 for traffic engineering information.
2. As we stated earlier, SPF is used to calculate the path for destinations. For traffic engineering, a slightly modified version of SPF is used, called constrained SPF (CSPF). With the extensions to link state protocols that Opaque LSAs and TLVs provide, a traffic engineering database is created that is only accessible by CSPF.
CSPF can understand that the link from R2 to R5 is 5 Mbit/s and does not satisfy the 6 Mbit/s tunnel constraint. So it will not take that path into consideration in its calculation.
3. If there is an appropriate path, the path is signaled by RSVP. Previously used to provide Integrated Services QoS, RSVP incorporated new messages, including path and reservation messages, to enable MPLS traffic engineering. Label information is carried within the reservation messages.
4. Once a path is signaled, traffic is put into the tunnel. This can be accomplished via many methods including static routing, policy-based routing, class-of-service-based tunnel selection (CBTS), policy-based tunnel selection (PBTS), autoroute, and forwarding adjacency. I'll discuss these methods in detail in a future post.
And in the next part of this series, I explain how to use MPLS traffic engineering path selection for bandwidth optimization.
About the Author
You May Also Like




