Spotting Network Vulnerabilities Before Hackers Do
To protect the network, you need to understand how attackers think and use their techniques to test your network security.
September 1, 2016

If there’s one thing I remember from Boy Scouts, it’s their motto, “always be prepared.” I soon learned that understanding the world from someone else’s point of view can also help you get ahead. Coincidentally, both of these life lessons apply to network security.
As many IT professionals have experienced firsthand, your network security strategy isn’t adequate if you only react to security issues after they occur; by then, it’s too late. To better lock down your data, you need to plan ahead by preparing and implementing a security policy that covers people, processes, and technology.
Additionally, to guard against growing security threats, you need to understand the tactics and exploits an attacker might use. To better protect your network from hackers, you need to think like one by figuratively stepping inside their shoes. This means attempting to penetrate your own network defenses using hacking techniques so you can identify network vulnerabilities before someone else does.
Hack your network
If a hacker’s goal is to connect to your network through unprotected WiFi and download sensitive data from file shares, would he or she be able to? Alternatively, could someone look through your windows to see passwords written on whiteboards or Post-it notes?
These are just a couple of scenarios that might be part of a penetration test, a systematic method of evaluating a network for common weaknesses. Enterprises often hire third-party security professionals to conduct these tests.
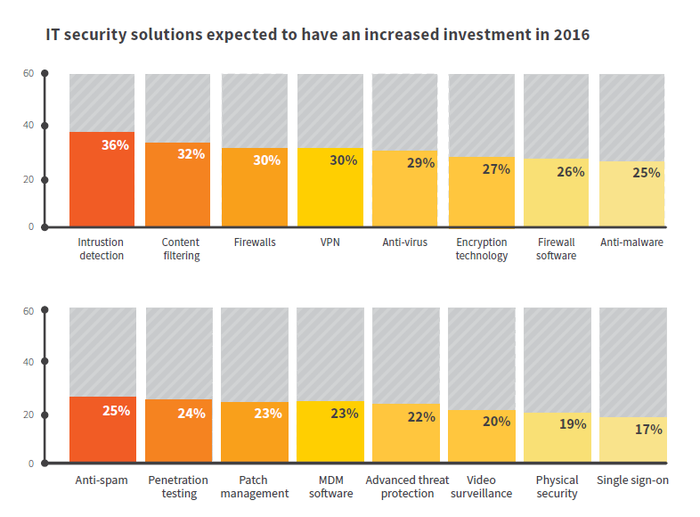
As big security breaches at prominent companies continue to make headlines, penetration testing of corporate networks is on the rise. According to a Spiceworks security report, nearly a quarter of organizations planned to increase spending on penetration testing this year.
IT Security Investments_Spiceworks.png
Boosting network security
There are a wide variety of weaknesses a good penetration test will try to expose in physical hardware, network infrastructure, operating systems, applications, data, or even employee behavior. Even if you don’t hire a security firm to evaluate your network, here are four tips to help you improve network security on your own.
1. Know what to defend
Do you know what PCs, servers, mobile devices, firewalls, and switches are on your network? That should be one of the first steps you take to secure a network. After all, a single weak spot in any of these could result in compromise. A network scanner can uncover PCs or servers running outdated firmware, end-of-life operating systems with known vulnerabilities, or no antivirus. After all, a hacker will go after the easiest targets first. For your firewall, a port scanning tool will help reveal whether your network is appropriately locked down or if you’re unnecessarily leaving ports open and exposing it to threats on the internet.
2. Train users on network security
Can employees tell the difference between a legitimate email and a phishing attempt? Do people know to never write down a password or give one to a stranger over the phone? Are they aware of the dangers of malware? Do they know not to trust links on the internet? You need proper training, reminder emails, and even periodic testing of users, or else hackers will likely have an easy time coaxing sensitive information out of employees.
3. Weigh defenses vs. threats
What defensive measures do you currently have in place, and are your network defenses appropriate for the corresponding security threats? For example, spam is a huge part of the phishing problem, so do your defenses include an effective email filtering solution? Similarly, because malware and ransomware affect companies worldwide, is your security solution up to the challenge? And do you have an intrusion-detection system to spot suspicious behavior on your network once someone gains unauthorized access?
If you work at a company that stores a lot of valuable data, the risk of being targeted is greater and you might need to up your game. Additionally, if you work in a regulated industry where the cost of a breach could ruin your company, you need to be even more careful.
4. Prioritize weaknesses and remediate
After you or someone else detects network vulnerabilities, it’s time to do something about them. It’s relatively easy to fix weak passwords, but guarding against more advanced threats might require investment in a security hardware or software. It makes sense to prioritize the threats with the highest probability of being exploited first.
It might also be necessary to educate management on security dangers so you can obtain the appropriate resources and budget to address problems. After all, the longer vulnerabilities go unaddressed, the more at risk you are to a hack.
By asking hard questions about your network and hacking it first, you can understand where your network is vulnerable, which empowers you to then address problem areas. And by knowing how networks could be attacked and preparing for the worst, companies can improve their security posture
About the Author
You May Also Like




