SASE Architecture: A Checklist for SASE-savvy Businesses
SASE provides secure and efficient access to cloud-based services and resources for users, regardless of their location. Follow this checklist to attain this goal.
May 1, 2024

Secure access service edge (SASE) provides companies a centralized means to manage, monitor, and optimize their wide-area networks, SASE solutions provide the flexibility to protect corporate assets, remote offices, and home-based and mobile employees, as security threats continue to evolve and rapidly increase.
Introduction to SASE Architecture
SASE is an architecture that provides converged network and security as a service with an array of cloud-based capabilities that can be located where and used when they are needed.
As such, SASE expands the perimeter to include all resources, regardless of their location or device. It provides a single and consistent security policy spanning all network and application assets.
Delving Deeper: Components of the SASE model
SASE architecture draws from a base of cloud-native security functions that include Secure Web Gateways (SWG), Cloud Access Security Brokers (CASB), Firewall-as-a-Service (FWaaS), and Zero Trust Network Access (ZTNA). These functions are provided as a service by a growing list of SASE vendors.
SASE architecture solutions can be categorized as provided by a single vendor, or in an integrated manner by multiple vendors. The emergence of single vendor SASE offerings provides businesses more options but more difficult choices.

Challenges in the Path of SASE Realization
Implementing SASE architecture solutions promises to recast your security approach for all those seeking access to lifeblood business applications for employees, trade partners, workers at home, and far-flung offices. The road to realization, however, contains many challenges for interested parties.
Complexity and Integration
Integrating SASE with existing IT infrastructure can be complex. Organizations often use a mix of cloud services, on-site data centers, and legacy systems, each with its own security and access controls. Attempting to ensure seamless integration without disrupting existing operations or creating cybersecurity gaps is an obstacle to success.
Performance and scalability
The SASE solution must scale to support growing numbers of users and devices while maintaining high performance for all services is essential. The solution? Balance security measures with performance to avoid latency or bottlenecks.
Cost management
Cost is an issue with any expansive IT implementation. And implementing an SASE solution is no exception. While SASE can reduce overall IT costs by consolidating services and reducing hardware dependence, understanding and managing these costs, especially in the transition phase, can be challenging. Companies must evaluate the total cost of ownership (TCO) and return on investment (ROI) carefully.
Customization and Flexibility
Each organization's needs are unique, and a one-size-fits-all SASE solution may not be suitable. Customizing solutions to fit specific business requirements while maintaining security and compliance standards requires a flexible approach from both the organization and the SASE provider. Work as a team.

Facing Off Against SASE Challenges
Businesses seeking to implement a SASE solution can meet the above listed challenges by taking measured steps. As the saying goes, Proper planning prevents poor performance. Careful unrushed planning is an important prerequisite process that can help deliver a smooth SASE solution and implementation.
Another foundational decision that falls under careful planning is determining who delivers the SASE implementation. Resource-rich businesses might prefer a DIY approach, while others may team with a vendor or service provider to handle this crucial undertaking.
Overcoming SASE Obstacles for Effective Implementation
Careful planning of a SASE implementation should include taking steps to ensure that your partner meets contractually agreed upon milestones for goals, SLAs for performance and time to respond/repair/solve problems, and legal agreements under which the customer avoids vendor lock-in by terminating the agreement a part of an exit strategy.
There are several questions you should address before undertaking an implementation. And there are several strategies to employ to ensure success. They include:
Determine what you need from SASE
Businesses must determine what capabilities they need from a SASE solution. Since it is likely they already use components of the security solution, this exercise should identify security gaps to be closed and weak areas to be strengthened.
Groups of SASE capabilities to focus on include SD-WAN, Cloud Access Security Brokers, Firewall-as-a-Service, and Zero Trust Network Access.
"You might already have many of these capabilities on your networks and at your edges. In other cases, there will be gaps in your security that SASE can fill”, explains Mary Shacklett, President of Transworld Data, a marketing and technology services firm.
Implement SASE incrementally – Start small
It is best to pilot-test the technology on a single, small network first to see how the SASE is working and how it integrates with your other security software, adds Shacklett. This gives you an opportunity to see where adjustments and modifications might be needed.
“From here, the best strategy for continuing to deploy SASE is to systematically move one network after another to the SASE service, making sure that everything is working properly before you move on to the next network.”
Review and enforce your user authorizations in SASE clouds
It is crucial that companies stay current when it comes to determining and updating which users are authorized to use, which IT networks and resources, and what the level of each user's access permissions is. A list of user authorizations and permission levels can be sent to the SASE provider or vendor. “Keep this list updated and current in the same way you maintain your internal user access authorizations and permissions with business managers,” advises Shacklett.
Implementing SASE: A Start-to-finish Checklist
Given the above-mentioned challenges and obstacles on the path to the realization of SASE, businesses should use the following checklist of items that must be addressed to help them plan for a successful SASE implementation.
Your step-by-step guide to adopting SASE should include the following:
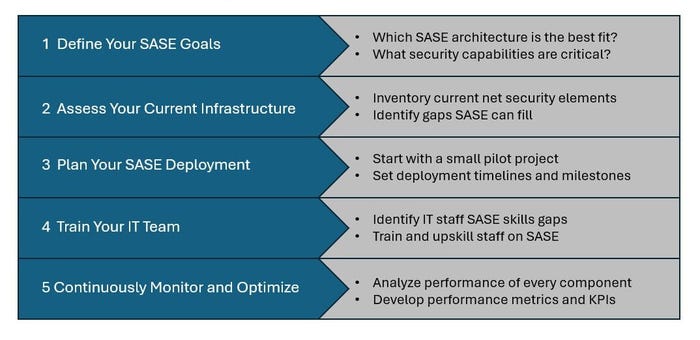
Define your SASE goals
What does your company seek to accomplish by implementing SASE? Learning the architecture and what you need in terms of security capabilities would be a logical starting point. Decide which of the discussed benefits – cost management, integration with current infrastructure, a single pane of glass for management and monitoring, and speed and flexibility to add and delete users, should be considered for the priority list.
Assess your current infrastructure
As a prerequisite to getting educated on SASE, your IT staff should inventory and rate the condition of what you are using now for networking security, network services, and supporting equipment (and the financial commitments of each). Identify gaps in your infrastructure that you believe SASE can close. Refer to the basic list of foundational SASE building blocks to determine what you need.
Choose the right SASE vendor
Choosing the right SASE provider is crucial, as it impacts the range of available features, scalability, and the ease of integration with other tools. There is also the risk of vendor lock-in, making it difficult to switch providers in the future if the chosen solution does not meet evolving needs. A big decision is whether to go with a single vendor or multivendor solution or to try a DIY approach. Seek market intelligence, read reviews, and connect with current SASE implementors. Do not forget to create an exit strategy should agreed-upon contractual commitments are not met.
Design and plan your SASE deployment
This checklist item is crucial to the success of SASE at your company. Work hand in hand with the vendor you selected to ensure that you share the same deployment details, milestones, and timelines. As mentioned above, it is best to start small with a pilot test in a single contained area to get first-hand experience from both parties. Having already inventoried your current infrastructure and what you seek to gain from a SASE solution, your path should be clear of major obstacles.
Establish a SASE governance framework
The importance of a SASE governance framework lies in its ability to ensure consistent security postures across an organization's distributed network, enhance visibility and control over data and users, and streamline security management processes, explains Mauricio Sanchez, Sr. Director, Enterprise Security & Networking Research at the Dell’Oro Group, a global market research and analysis firm. “This approach not only mitigates risks associated with digital transformation and remote work models but also optimizes performance and user experience, making it a critical component of modern cybersecurity strategies.”
Train your IT team
Implementing and managing a SASE architecture requires new skill sets and knowledge. Organizations may face challenges in upskilling existing staff or recruiting new talent with the necessary expertise in cloud-centric networking and security. Be sure to investigate training programs offered by some SASE solution providers, such as Cato Networks. If your provider doesn't offer one, consider an independent offering to supplement the training.
Continuously monitor and optimize
Your company will benefit from the continuous monitoring and optimization of your complex SASE solution. Your solution must combine SD-WAN, routing, and encryption with security capabilities to deliver the best user and application experience while also enforcing all aspects of security, according to Jon Taylor, director and principal of security at Versa Networks. Another must: the solution “must have a single, unified management system that provides full visibility and analytics for every component of the SASE ecosystem, including work-from-anywhere entities,” he added. It must be optimized for software as a service and performance.

SASE Architecture Checklist: A final word
By integrating network security functions with wide area networking (WAN) capabilities, SASE aims to provide secure and efficient access to cloud-based services and resources for users, regardless of their location.
Attaining this goal, however, requires companies to review their needs, learn the SASE architecture, address issues, and take steps on the path to realization using this checklist – and expert guidance to optimize and streamline an otherwise complicated and complex undertaking.
SASE provides secure and efficient access to cloud-based services and resources for users, regardless of their location. Follow this checklist to attain this goal.
About the Author
You May Also Like




