Nmap Tutorial: Host Discovery
In this excerpt from "Nmap: Network Exploration and Security Auditing Cookbook - Second Edition," learn how to perform a ping scan to find live hosts in your network.
June 20, 2018

Finding live hosts in your local network is a common task among penetration testers and system administrators to enumerate active machines on a network segment. Nmap offers higher detection rates over the traditional ping utility because it sends additional probes than the traditional ICMP echo request to discover hosts.
This recipe describes how to perform a ping scan with Nmap to find live hosts in a local network.
How to do it...
Launch a ping scan against a network segment using the following command:
#nmap -sn
The results will include all the hosts that responded to any of the packets sent by Nmap during the ping scan; that is, the active machines on the specified network segment:
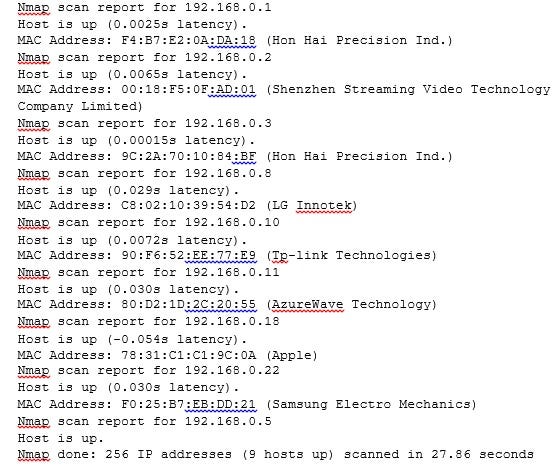
image 1_4.jpg
Ping scans in Nmap may also identify MAC addresses and vendors if executed as a privileged user on local Ethernet networks.
How it works...
The Nmap option -sn disables port scanning, leaving the discovery phase enabled, which makes Nmap perform a ping sweep. Depending on the privileges, Nmap by default uses different techniques to achieve this task: sending a TCP SYN packet to port 443, TCP ACK packet to port 80 and ICMP echo and timestamp requests if executed as a privileged user, or a SYN packets to port 80 and 443 via the connect() syscall if executed by users who can't send raw packets. ARP/Neighbor Discovery is also enabled when scanning local Ethernet networks as privileged users. MAC addresses and vendors are identified from the ARP requests sent during the ARP/Neighbor Discovery phase.
There's more...
Nmap supports several host discovery techniques, and probes can be customized to scan hosts effectively even in the most restricted environments. It is important that we understand the internals of the supported techniques to apply them correctly. Now, let's learn more about host discovery with Nmap.
Tracing routes
Ping scans allows including trace route information of the targets. Use the Nmap option -- traceroute to trace the route from the scanning machine to the target host:
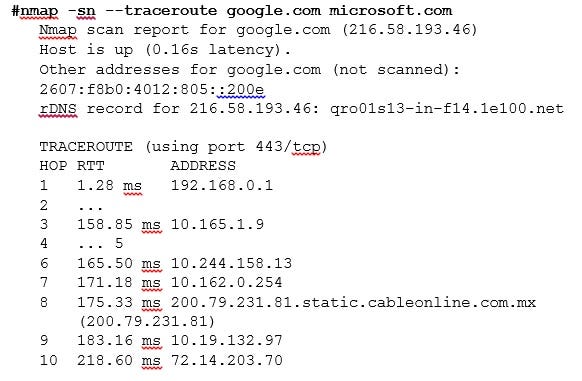
image 2_4.jpg
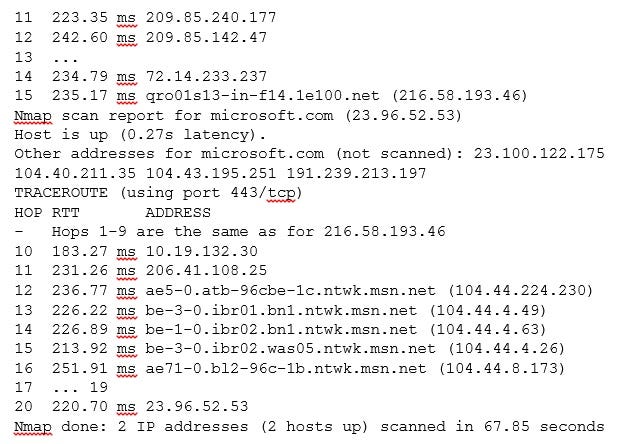
image 3_4.jpg
Running the Nmap Scripting Engine during host discovery
The Nmap Scripting Engine can be enabled during ping scans to obtain additional information. As with any other NSE script, its execution will depend on the hostrule specified. To execute a NSE script with ping scans, we simply use the Nmap option -- script , the same way as we would normally call NSE scripts with port/service detection scans:
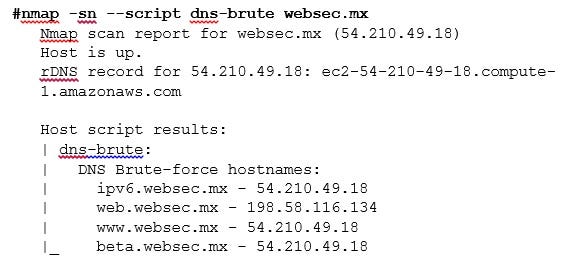
image 4_3.jpg
Another interesting NSE script to try when discovering live hosts in networks is the script broadcast-ping:
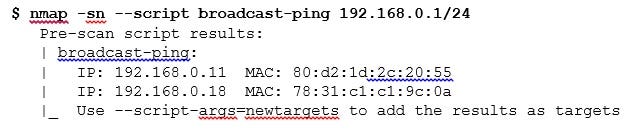
image 5_2.jpg
Exploring more ping scanning techniques
Nmap supports several ping scanning techniques using different protocols. For example, the default ping scan command with no arguments (nmap -sn ) as a privileged user internally executes the -PS443 -PA80 -PE -PP options corresponding to TCP SYN to port 443, TCP ACK to port 80, and ICMP echo and timestamps requests.
In Chapter 2, Network Exploration, you will learn more about the following ping scanning techniques supported in Nmap:
-PS/PA/PU/PY [portlist]: TCP SYN/ACK, UDP or SCTP discovery to given ports
-PE/PP/PM: ICMP echo, timestamp, and netmask request discovery probes
-PO [protocol list]: IP protocol ping
This tutorial is an excerpt from "Nmap: Network Exploration and Security Auditing Cookbook - Second Edition" by Paulino Calderon and published by Packt.
About the Author
You May Also Like




