The New Normal Requires a New Enterprise Security Framework
Managing network architecture while moving to SASE requires pragmatic, secure access solutions for existing hybrid infrastructures that are future-compatible.
November 30, 2020

When COVID-19 forced office closures, enterprises either fast-tracked digital transformation initiatives or expanded IT resources to mobilize remote workers. Enabling hundreds, even thousands, of remote workers stretched traditional enterprise network security stacks to their limits, straining infrastructure and exposing network vulnerabilities – inside and out.
Many organizations have begun to accelerate the movement of their IT resources and workloads to the cloud. This has generated momentum for the adoption of Secure Access Service Edge (SASE)—Gartner’s network security framework based on an identity-driven, cloud-native, globally distributed platform that securely connects users to applications wherever they reside (WAN, cloud, mobile, and IoT).
While the future of network security is certainly SASE, much of the current state of enterprise networking is earthbound. Managing network architecture while organizations transition to SASE requires pragmatic, secure access solutions for existing hybrid infrastructures that are future-compatible.
Network Security in Transition
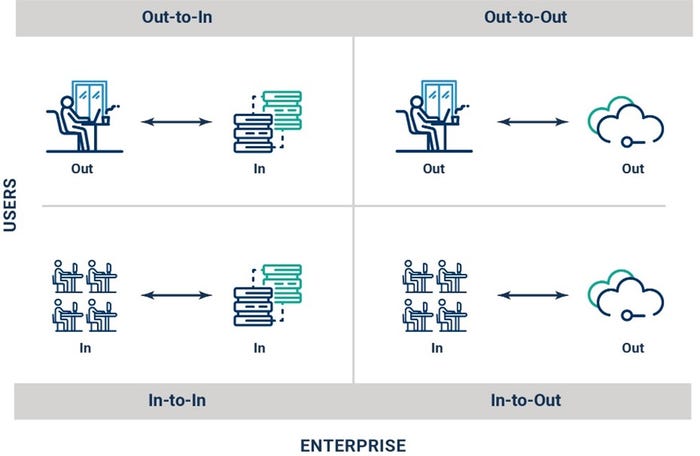
Secure access requirements for enterprises have taken on a new paradigm. Some applications are on-premises, while others are in the cloud, and some users are on-site, while others are remote. Network security requires a new model that considers all scenarios and positions organizations for the move to SASE, including:
Out-to-In: Remote workers need access to private apps or resources that reside within the enterprise local area network (LAN).
Out-to-Out: Remote workers need access to corporate apps that are located on the public cloud or internet.
In-to-Out: On-site workers who are connected to the enterprise LAN require access to corporate apps on the public cloud or internet.
In-to-In: On-site workers who are connected to the enterprise LAN require access to corporate apps located on the enterprise LAN.
Ericom.jpg
Let’s look at each of these scenarios to understand the issues and identify potential solutions.
Out-to-In
When remote workers need access to private apps or resources on the LAN, organizations need to administer least-privilege zero trust access for authenticated users. This approach eliminates the implicit trust typically granted by most current security architectures once a user is connected inside the corporate network.
In this scenario, Zero Trust Network Access (ZTNA) capabilities can be used to secure all remote interactions with network apps, data, and resources, enhancing VPNs and NGFWs and enabling micro-segmented access to network resources and applications. Technologies such as multi-factor authentication (MFA), identity-based segmentation, and software-defined perimeter (SDP) further secure and strengthen granular, per-user policy access.
Out-to-Out
Remote workers need access to corporate SaaS apps in the public cloud as well as general internet and web-based resources, but it is inefficient to route this traffic through corporate security stacks in the datacenter. Organizations must secure this “direct-to-net” traffic with new approaches.
With cloud-delivered remote browser isolation (RBI) services, which air-gap all web interactions away from endpoints in secured cloud containers, and MFA and cloud access security broker (CASB) capabilities, organizations can control access to the web and without inefficiently routing traffic through corporate data centers.
In-to-Out
Every user working in the office accesses the public internet via the corporate LAN — email and cloud apps are among the most important use cases. While internet access is essential for productivity, it is the top threat vector for executing cyberattacks since the majority are initiated via phishing emails or malicious sites.
RBI-as-a-service is a next-generation web security tool that safeguards enterprise networks by proactively preventing web and email-based malware and ransomware attacks. It ensures users can use their devices to safely access any site or web app that is necessary without compromising their devices or networks.
In-to-In
On-site workers who are connected to the enterprise LAN and need access to local corporate network apps should be treated the same as anyone who gains access from outside the network perimeter, as in the Out-to-In scenario. Surprisingly, that is often not the case. In this scenario, internal traffic must be subject to least-privilege access controls. For example, applications authorized users are not permitted access to would be invisible to them (e.g., cloaked from their network visibility). Additionally, in this environment, any unauthorized users who somehow breach the network would be left completely in the dark.
If possible, creating granular, per-user authorization policies will limit access to the most secure level possible. AI/ML tools should be investigated to help in the “heavy-lifting” of creating these types of policies. Identity-based micro-segmentation solutions can be used to enforce least-privilege access policies I described, as well as cloak applications from cybercriminals.
Moving Toward SASE
Organizations are starting to transition toward the SASE security framework. During this time when remote work has been the focus, the Out-to-In and Out-to-Out access paths are getting the most attention. This new enterprise security framework includes the other scenarios and encourages a comprehensive approach to network security using user and resource location to ensure that all access options are secured.
David Canellos is President and CEO at Ericom Software.
About the Author
You May Also Like




