Network Access: It's Not Simple Anymore
Configuring access to corporate resources is multi-faceted in the age of the digital workspace.
March 30, 2016


1-communication.jpg
People work digitally. So it's more important than ever for organizations to effectively manage endpoints and access.
Generally speaking, IT has used three different technologies to achieve this: Virtual desktop infrastructure (VDI), Identity and access management (IAM), and service management. Those technologies alone are proving insufficient to address the new challenges of how employees work, however.
VDI. Virtual desktop infrastructure is just that: infrastructure. It can offer an effective means of storing virtual desktop images and delivering those desktops out to users within the enterprise and/or working remotely. VDI itself does not, however, provide policy-based control over exactly which resources are on any particular user's desktop.
IAM. Identity and access management is an essential gatekeeping function for allowing appropriate access and blocking inappropriate access. But, as with VDI, IT still needs a means of "telling" the IAM control layer which resources any given user should or should not have rights to at any given time.
Service management. Service management offers IT a way of cataloging and managing the delivery of digital resources to users. Its focus, though, is on the services themselves -- rather than individual users and their appropriate permissions at any given time or place.
IT's challenge, in other words, is how to orchestrate disparate technologies -- including VDI, IAM, service management, mobility management, enterprise app stores, and the like -- to ensure that people get immediate access to the corporate resources they require to be optimally productive, while at the same time ensuring that people don't have access to resources to which they are not entitled.
(Image: Sigal Suhler Moran/iStockphoto)

2-coffeeshop.jpg
3 core challenges
From a technical perspective, there are three operational considerations are making access management more challenging than ever for IT.
Morphing service portfolios
Once upon a time, users needed little more on their desktops than a few desktop productivity tools and a database or two. Today's tools have expanded to include:
Email, telephony, and collaboration
Workflow/process applications
Databases
Document repositories
SaaS/cloud services
BI and analytic tools
Mobile device provisioning/permissioning
Employee support services (benefits administration, education programs, etc.)
Not everyone needs every resource in the enterprise portfolio. And access to many resources must be tightly restricted because of governance constraints on PII and other data. The resulting complexity of resource-to-user mapping makes access management inherently difficult.
The multi-device user
Most organizations' highest-value employees constantly move across multiple devices. One minute they're working from their desktop PC. The next minute, they're using a Droid smartphone. Then they're on an Apple laptop or iPad.
These people can't have their productivity constrained by their choice of device at any given moment. Instead, they need to be able to work with whichever device is more convenient for a given place and time. They might find their smartphone most convenient when they're really on the move, while their laptop or tablet is more convenient when they can sit for a moment in a waiting area or coffee shop.
VDI facilitates this cross-device productivity by abstracting applications and other digital resources from the endpoint device and its particular operating system. However, as noted earlier, VDI only provides a mechanism for allowing endpoint devices to access centrally managed desktop resources. It does not inherently provide policy-based governance to make sure that the virtual desktop instance provided to any given user is the right one for that particular user under their current conditions.
Permission in context
Digital workspace management is made still more challenging by the fact that people are constantly working in different situations. These situations often have an impact on whether a given resource should be made available to them at a particular moment.
Situation contexts that can impact resource authorization include:
Time of day
Location (campus geofencing, national boundaries, etc.)
Network connections (e.g. public Wi-Fi hotspots)
For example, mobile users might be permitted to access document sharing generally even when they are out of the office, but access to certain repositories of sensitive corporate IP or customer information might be restricted when they're sitting in a coffee shop using an unencrypted public Wi-Fi connection.
Smart management of employee access is thus optimally not just driven by individual users' roles and responsibilities—but also by real-time session-specific context.
(Image: Berc/iStockphoto)
3-workspace mgmt.jpg
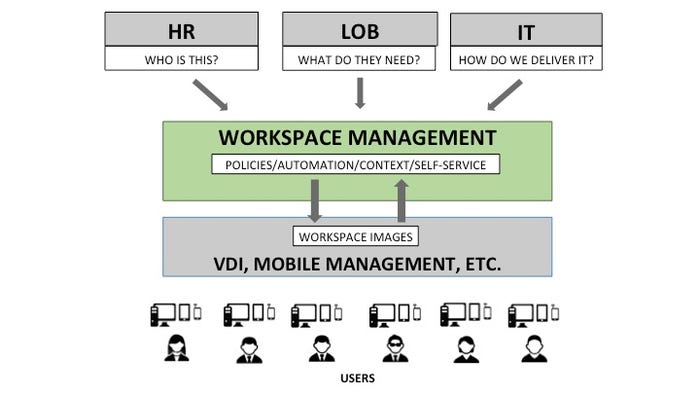
Managing the whole
Conceptually, management of these elements can be enabled by a layer of abstraction between service management and desktop delivery, often called workspace management. This layer of abstraction provides several key capabilities:
Policy: Effective management enables IT and the business to collaboratively define policies for who gets access to what, and under what conditions. These policies are essential for automating resource permissioning while fulfilling security and compliance imperatives.
Automation: The automation of resource provisioning eliminates the latencies that result when service requests have to be manually executed by IT staff. A single point of control for provisioning automation also eliminates the problems that arise when IT staff keep writing individual provisioning scripts on an ad hoc basis over time -- and store them in random places.
Integration: A layer of management acts as an integration hub between service management, VDI, HR applications (which can trigger provisioning changes), mobility management (which can provide important session context data), and any other system relevant to user access.
Self-service: At most organizations, changes in user access aren't exclusively driven by business policies. Line of business managers and users are also free to make certain decisions about digital resources. A management system should provide for this business self-service.
Reporting: Access management should give managers visibility into key metrics and events such as rejected requests, failed provisionings, user uptake rates, etc. In more advanced scenarios, visibility into service cost per user can be calculated.

4-office.jpg
Employee access stages
Often, access management can be divided into three stages: on-boarding, employment, and off-boarding.
On-boarding: In the on-boarding stage, new employees are provided with the initial digital resources they need to do the jobs for which they are first hired, but at many companies, it is not unusual for new employees to wait days, week, or even months for some services. These delays have a variety of adverse consequences, including low productivity, costs, and the encroachment of shadow IT.
Slow initial provisioning can be even more problematic for companies that need to be able to bring on temporary and/or seasonal employees quickly to deal with spikes in demand.
Employment: Once employees are on-boarded, things can get even more complicated. People get promoted, transferred, and reorganized, requiring changes in access requirements. The consequences of any latency between job change and resource provisioning can be similar: lost productivity, lower employee engagement, impaired business agility, and the security/compliance exposures that result from ad hoc employee work-arounds.
As with on-boarding, many aspects of job change can be addressed by having HR events trigger appropriate changes to the digital workspace—with check-box approvals by human managers as a safeguard. But because changes in job responsibilities among the active workforce are not always as cut and dried as those of a brand-new hire, more self-service means of desktop resource activation are also important.
Off-boarding: While often-neglected, off-boarding is extremely important. Any failure to remove user accounts as soon as employees are terminated or change positions can result in significant security and compliance exposures.
Unfortunately, it is not unusual for organizations to have user accounts lingering long after that user has left the company, leaving organizations vulnerable to malicious activity from disgruntled ex-employees or from cyber-criminals. In addition, such accounts can be deemed a regulatory violation by IT auditors.
Access management can serve as a central point of administration for all digital services, allowing elimination of all user privileges completely and immediately.
(Image: mutsmaks/iStockphoto)

5-speed.jpg
Smarter access management
The design and implementation of well-automated, policy-driven access management strategy requires thought, effort, and money. But it can be well worth it for organizations that recognize the need to take friction out of service delivery to an increasingly mobile workforce under dynamic business conditions.
Key benefits include:
Elimination of the productivity lost as a result slow on-boarding and slow provisioning of services for employees when they move into new positions
Greater organizational agility
Mitigation of security and compliance risks associated with failure to immediate inactivate user accounts when an employee is fired or transferred to another position
Freeing IT staff from a high volume of housekeeping tasks
Higher ROI on investments in new digital services through faster, broader user uptake
Better long-term engagement with tech-centric employees whose tolerance for unresponsive, non-consumerized corporate IT continues to decline
For these reasons and others, IT leaders -- as well as their peers in HR and the CFO's office -- may want to consider a fresh approach to access management that get the right resources to the right people at the right time with less manual work and less opportunity for costly errors.
(Image: artisteer/iStockphoto)
About the Author
You May Also Like




