In-car networks are increasingly being designed-in and deployed to connect systems such as infotainment, driver assist, autonomous driving and safety systems, often on shared, high-bandwidth infrastructures. These networks, and the devices that connect to them, require diagnostics and service through external interfaces. Additionally, more and more of today’s connected cars are equipped with Internet access, and oftentimes a WLAN, to communicate with devices inside and outside of the vehicle.
Consequently, the connected car could also become a prime target for hackers. Using just a laptop or tablet, hackers have the potential to take control of the electronics in your car. There is already research today that documents and demonstrates such attacks with alarming consequences.
In contrast to traditional IT networks, the in-car network is manufactured and physically insecure. So, with access to a mass produced vehicle and the appropriate time and resources, a hacker can develop a set of “attacks” against the vehicle and then distribute those attacks through an entire fleet. In other words, a single, well-engineered attack could have a wide impact.
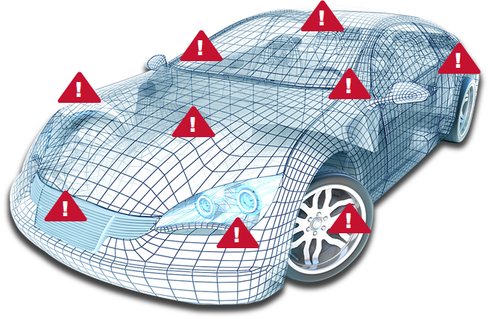
Figure 1:
Figure 1. The connected car is vulnerable to attacks at many different entry points into the network via firmware corruption or through an Ethernet on-board diagnostics port, Ethernet port access or gateway device. The types of attacks that can occur include network control (hackers install or corrupt a device on the network so they can control the operation of other devices), denial of service, and snooping (information theft).
Increasingly, Ethernet is being designed into in-car networks because of its high bandwidth, price-performance, ubiquity, and future technology roadmap, while new standards such as single twisted-pair and Audio Visual Bridging (AVB) are opening up many new automotive use cases. Ethernet's already in some vehicles today.
By 2020, Frost and Sullivan estimates that most cars will have 50 to 60 Ethernet ports, with premium vehicles pushing that number toward 100. Even entry-level vehicles are expected to get in on the action with roughly 10 Ethernet ports.
Ethernet, particularly switched Ethernet, has been deployed in IT environments for several decades and has a long history of standards and solutions that can help secure the network.
To better understand how Ethernet can help secure the connected car, it’s important to first understand some basics about the technology. As shown in Figure 2, Ethernet uses a standard packet format that includes a source and destination address, a VLAN tag and a Frame Check. This provides a basic level of authentication, isolation and data integrity. The addresses can be globally unique or locally administered (given that the in-car network is mostly a closed network).
The Ethernet switches provide traffic isolation and filtering using a Filtering Database (FDB) or Multicast Forwarding Database (MFDB), and can act as management points for further network control. A rich set of statistics standards enable anomaly monitoring in software.
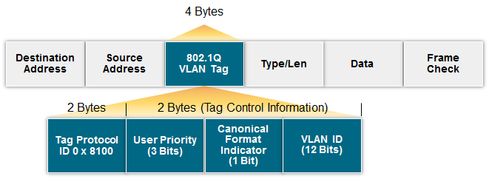
Figure 2:
Figure 2. The Ethernet frame's header contains destination and source MAC addresses as its first two fields and a cyclic redundancy check (CRC) to verify packet integrity. It may also contain a VLAN tag, which defines a system and procedures to be used by bridges and switches to support VLANs.
Switched Ethernet offers a base level of security protection, but more is needed, and many additional features have evolved and are widely supported in Ethernet standards and/or products. Because the in-car network is typically highly-engineered and static with predictable traffic characteristics, it offers the opportunity to tightly configure and constrain the network operation according to design intent.
For instance, there are several ways to control the scope of network traffic and in turn, the potential for snooping and attack. One approach uses VLANs to create multiple broadcast domains within the physical network (see Figure 3); this is already broadly deployed and supported by Ethernet switches. Using VLANs, you can isolate traffic of different types on the shared physical network such that devices can only talk to the other devices within their domain. For example, one VLAN can be configured for Infotainment while a separate one can be configured for driver assist and another for safety.
Network isolation between the two can be enforced by the Ethernet switches. Traffic isolation also can be achieved within each VLAN through the use of unknown unicast or multicast filtering. Rogue stations and MAC spoofing can still occur, but techniques such as static provisioning of the FDB, port MAC locking, and implementation of software learning limits can all be used to mitigate this risk.
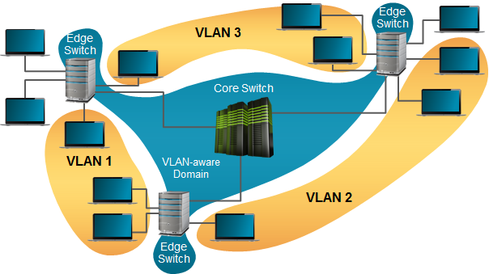
Figure 3:
Figure 3. VLANs can be used to limit the scope of traffic and mitigate the risk of attack. Note that no connectivity exists between the VLANs themselves without a router.
In addition, access control lists (ACLs) can reduce the scope of traffic and are particularly well suited for the in-car network because of the opportunity to design in knowledge of expected device and network behavior. ACLs provide precisely configured match-action rules for packet forwarding that define which stations can transmit and where the traffic is allowed to go.
NEXT: More security features